What is the purpose of a client certificate in GlobalProtect VPN?
The primary purpose of a client certificate is to verify the device’s identity cryptographically and sometimes the user’s identity before granting VPN access. You may think, Okaay? What do you mean by verifying a device’s identity, and sometimes users?
Well, in practice, this means the following:
- Only trusted devices can connect (not just users with stolen credentials).
- Prevents unauthorized, unmanaged, or rogue devices.
- Enables mutual authentication (client proves identity to the firewall, not just the other way around)
- And finally, Adds a strong security layer before SAML / LDAP / MFA even runs.
Let me explain with a visual example.
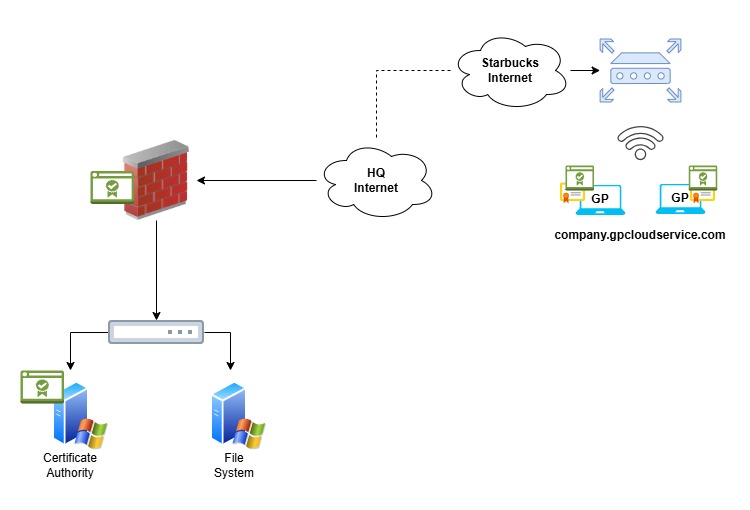
The servers
The organization has a Certificate Authority (CA) that acts as the trusted root or intermediate CA for issuing and validating client certificates. The file server is an internal resource that remote users access after successful VPN authentication.
The Firewall
The firewall gets a copy of the CA (root or intermediate) certificate to trust and validate the client’s certificate. Then, the firewall uses a certificate profile to validate the client certificate presented by the GlobalProtect app during the connection process.
The Client Computer
The remote user has a client certificate (with a private key) and the trusted root/intermediate CA certificate. If the client certificate is missing, invalid, or untrusted, GlobalProtect will fail to establish the VPN
What Problem Does a Client Certificate Solve?
Typically, traditional VPN access relies on
- Username + password
- Sometimes MFA
The problem
- Credentials can be phished
- MFA can be fatigue-attacked
- Stolen credentials can be reused from any device
- A client certificate binds access to a trusted machine, not just a user.
- If the certificate is missing, the connection is denied, even with valid credentials.
Goal of a Client Certificate?
To prove the identity of the device (and sometimes the user) before allowing VPN access. Even if the username and password are correct, access is denied without a valid client certificate.
Think of it as a strong pre-authentication layer, not just another password.
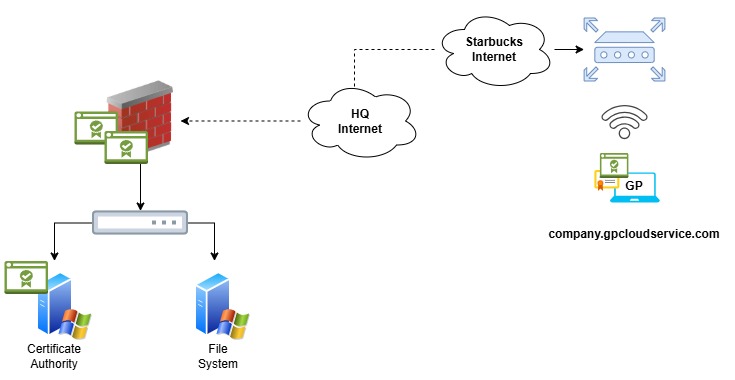
Here Is an Analogy
A user accidentally leaks their VPN credentials. An attacker attempts to connect to GlobalProtect using the stolen username and password. However, the connection is denied immediately because the attacker’s device does not have a valid client certificate trusted by the organization.
Despite having correct credentials, the attacker cannot access the network because device trust is required in addition to user authentication.
In Summary
Credentials can be stolen, but trusted devices must be proven.
Need Help?
If you or your organization are having a little trouble getting this service up and running, don’t worry. We’re here to help! Just give us a call or send us a message, and we’ll be more than happy to help you get everything set up smoothly.
Cheers,


